seccomp-nurse is a sandboxing framework based on SECCOMP. It is
designed to run applications in a kind of jail (enforced by the
kernel). It does not use ptrace() at all.
Architecture
seccomp-nurse uses two processes, one running the "untrusted code"
and the other is the helper, it is the referee between the
untrusted process and the kernel.
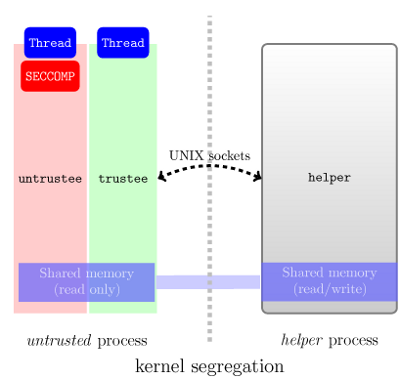
Because a SECCOMP process can only call read, write,
sigreturn and _exit, this is insufficient to execute even the
simplest binary. To work around this limitation, the untrusted process is splitted into two threads (called untrustee and
trustee):
- The untrustee runs the untrusted code, syscalls are trapped and handled by the helper.
- The trustee has only one task: do whatever the helper orders. It has zero interaction with the untrustee, considered hostile.
The helper is a Python application implementing access control:
when a syscall is called in the untrustee, the helper is
notified and takes the decision to deny, deleguate it to the
trustee or let the untrustee execute the syscall (if the syscall
executed by the untrustee is not allowed by the kernel, it will be
killed by SIGKILL).
How to use it?
$ git clone git://github.com/nbareil/seccomp-nurse.git $ cd seccomp-nurse/ $ make $ ./sanbdox -- /usr/bin/python
Easy, isn't it?
Screencast
Here is a demonstration
of seccomp-nurse running the python interpreter in the sandbox. The purpose of
this video is to show the ACL engine configured to restrict
the open() syscall to whitelisted directories only
(/secret not being included obviously). However,
access() ACL was configured to always return "OK", thus, it is
accessible from the interpreter.
Status
- : Thanks to Fabrice Desclaux, security issues were addressed and sockets are now supported! The targeted application was the HTTPD daemon from libevent
-
(commit 588b381d):
seccomp-nursecan run pdftotext successfully! Woo! However, there is still a lot of things to do, see the commit message to get an idea.Updated @ : it even runs the Python interpreter !
/usr/bin/pythonjust need to be compiled with--disable-shared!
Current limitations
-
dlopen()not supported yet -
clone()(sofork()and threads) is not (yet?) supported -
socket()support is almost ready -
exec*()will never be supported - Signals not supported
At the moment, there is no security check implemented. The sandbox is wide open! It will be the next step.
References
- Ekoparty's slides
- Blog post about "SECCOMP as a sandboxing solution?"
- Blog post about "How system calls work on Linux?"
- Chrome browser:
Availability
Releases
No release has been made yet but you can clone the development repository!
Sources
seccomp-nurse is a free software available under the GNU Public
Licence 2! Sources are availables on github: http://github.com/nbareil/seccomp-nurse/
Acknowledgment
This work was funded by the European Commission under contract IST-FP6-033576 (through the XtreemOS project) and EADS Innovation Works.